Brute force Nortel IP-8815 with Hydra
Spoiler: Your IP-8815 telephone is blocked by a password that you do not know… It may be possible to find it by leaving this thankless task to a faithful program, Hydra. here’s how.
When we acquired our IP-8815 phones, we were lucky because they weren’t blocked and we were able to reset them directly through the phone.
But some have not had our luck and have phones blocked by a password: on the web interface, but also on the phone itself. It is therefore impossible to reset it easily.
So, before taking out the soldering iron hoping to aim for the right electronic component (and break everything), try random combinations (and go crazy), or sue your correspondent for inadequacy of the thing sold (and benefit from a non-suit), we offer you an alternative.
For some firmware, you could dial
**73639[MAC]##whereMACis the MAC address number (written on the back, and inside the phone), and where the letters are composed via the corresponding key (e.g. A, B and C are on key 1). Personally, this technique did not work on ours.

We will ask a program to find the password of the web interface by trying them all and warn us when it has finished. It is called a brute force, or a brute force attack if we want to be more chic.
On the other hand, we do not say that we invoke brute force (I assure you that I have seen this in French reports). It’s sound Star Wars but it mostly shows that the person used an automatic translator.
Get Hydra
Hydra is software specifically designed to attempt authentication with a set of logins and passwords until the right combination is found. Exactly what we need today.

It was developed in the heyday (when I fell into the pot, early 2000s; anyone telling you it was better before is an old reactionary, and those who say it’s better now are young novices who lack experience) by the THC team whose members have subsequently converted to the IT security industry. Not having been equaled since, it continues to be used.
Linux
If you are on Linux, you can install the package hydra
(in command line) or even hydra-gtk to have a graphical
interface. On ubuntu you could use this line:
sudo apt-get install hydra-gtkFor centos, you would first have to enable EPEL repositories
but then you will have the hydra package.
Windows
There are several versions of Hydra for Windows (at clubic) but as I don’t know who compiled them and therefore if the files are healthy or if it’s Trojans, I’ll let you choose…
Personally, if you hesitate, prefer the next option with Kali.
Kali
Personally, it’s still the method I prefer because it avoids polluting my systems with tools that I will only use once.
For those who don’t know it, Kali Linux is a distribution that embedded a whole bunch of penetration testing tools and, to top it off, can be used without install.
So I advise you to download Kali Linux and burn the ISO image to a DVD. Once the DVD is ready and inserted into a computer, restart it and let Kali start.
For Windows 10 users. It may cheat and always (re)start Windows. Quick tip: when you click on reboot (in the menu or on the welcome screen), leave the shift key pressed and your Windows will then offer you menus to enter the BIOS/UEFI and, ultimately to boot from the DVD.
Once the system has started, you can launch Hydra via the menu (blue icon with the dragon), and rather than search, you can type hydra and it will offer you relevant results (without even needing your personal data and geolocating you. Cortana, Siri and Alexa, I see you 😉).
Use Hydra
Depending on your systems and the version you’re using, the menus may change slightly, but since these GUIs are just decorations around the command-line tool, whatever version you’re on, you should be fine.
Target
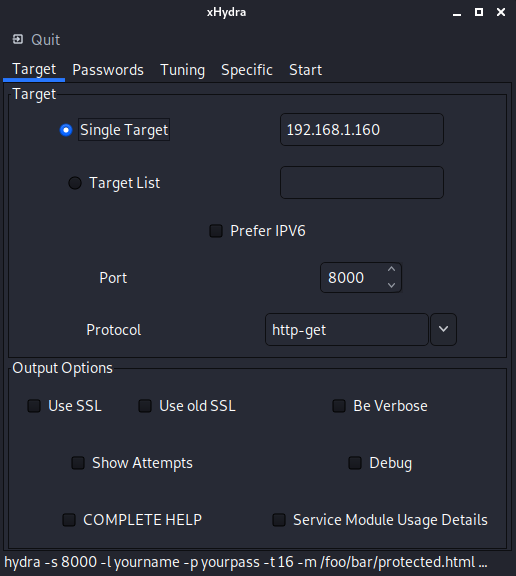
The first tab allows you to configure the application targeted by our brute force attack. Here we are going to fill in the parameters corresponding to the configuration web interface of our IP-8815.
- Single Target: for the phone’s IP address, in our
case,
192.168.1.160, - Port: for TCP port number, for IP-8815,
8000, - Protocol: for the authentication method used, for
IP-8815,
http-get.
The other fields do not interest us. You can then click on the next tab (Password).
Passwords
This tab allows you to customize the attack itself by choosing the sets of identifiers (login and passwords) to test.
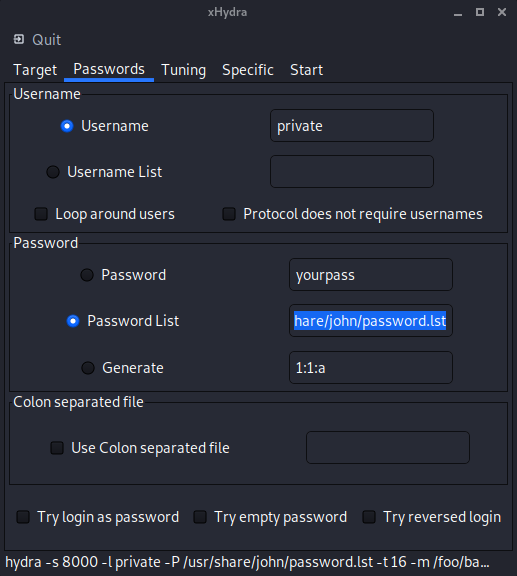
- Username: we choose username and fill in
the unique username of IP-8815,
private - Password: we choose Password list and by clicking in the area, we choose the file containing the list of passwords to use.
You could search and download your own password files. On Kali, there
are already some provided in
/usr/share/john/password.lst.
You could check the boxes at the bottom of this screen (for us it was not useful). We can then move on to the next tab, Specific (because we have nothing to change in Tuning).
Specific
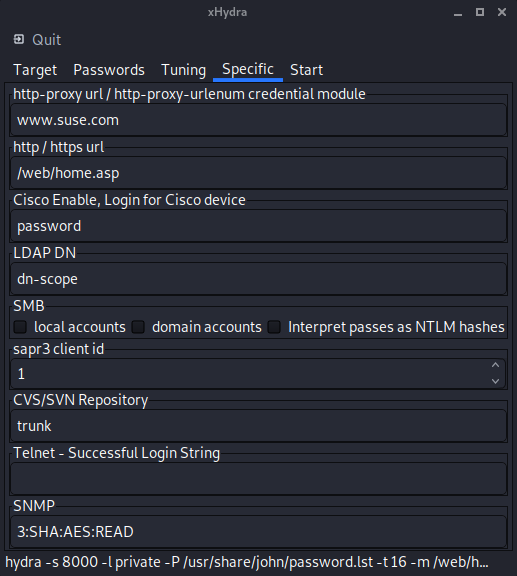
This screen allows you to configure too many things at once but we have to go through here because we have to fill in the page of the web interface of the phone that we want to access so that Hydra can attempt authentications.
- http / https url: corresponds to the path in the
address of the page to be tested, for our phone,
/web/home.asp
We have nothing else to configure here and can leave the default values. We then go to the last tab, Start.
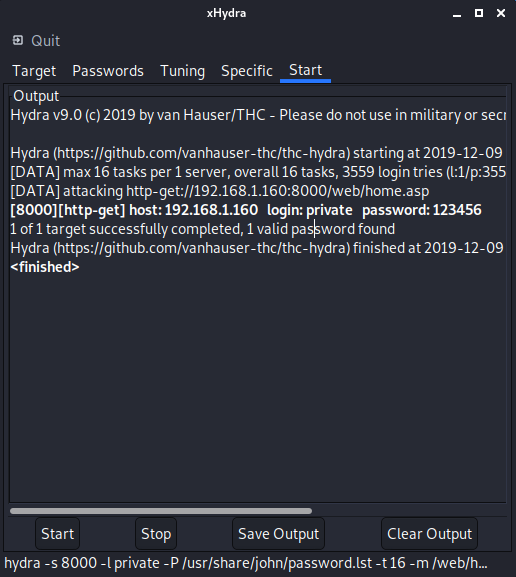
Start
Difficult step, we simply click on the Start button (at the bottom) and we wait for the magic to work.
In our case, the password was particularly easy and it only took 3559 attempts to discover that it was
123456. If your phone password is longer, you may need to wait a little longer.
Now all you have to do is log in on the phone with the password that Hydra has kindly discovered for you.
Reload configuration
With all this, we almost forget that we are there to reset the phone. To do this, click on Load default configuration (at the bottom of the menu on the left).
We then click on Load and we wait for the phone to
finish restarting.
Once restarted, the phone is then like a new one and is no
longer blocked (password on the phone directly). FYI, the web interface
having returned to its default settings, the password is now
lip.
Secure your phone
If you don’t want to fall victim to this attack on your turn, it would be a shame after all this effort, you can use the following two solutions together:
- Use a strong password, i.e. long and complex,
- Use a dedicated network, and avoid anyone being able to connect to your phones.
Of course, that won’t prevent a physical attack. By connecting
directly to the phone (or stealing one) but that will always be more
efficient than leaving them lying around on the LAN with
123456 as a password.
And after
Now that your phone is unlocked, you can set it up.
- Configuring IP-8815 Phones
-
April 1, 2019 Now that we have two phone lines and an IPBX to rule them all, we will be able to se play pro with SIP phones.
- Configuration of a VitalPBX SIP server
-
March 25, 2019 Now that our analog lines are managed by a gateway, it remains to interconnect it with our IP phones. For this, we will install a SIP server, VitalPBX, to register and communicate all our equipment.
 Disponible
Disponible